A module contains a group of functionality. In fact this also means you need to be aware of values set by the lower configuration layers including defaults to properly override. P6OutageFactory - for outage functionality , see [ P6Outage ] p6outage. It is recommended that you include this category. Disable or enable the P6Log module by editing the spy. Otherwise , it fills in the values of the Prepared Statement so you can see the effective SQL statement that is passed to the database. No other statements are logged except the long - running statements. 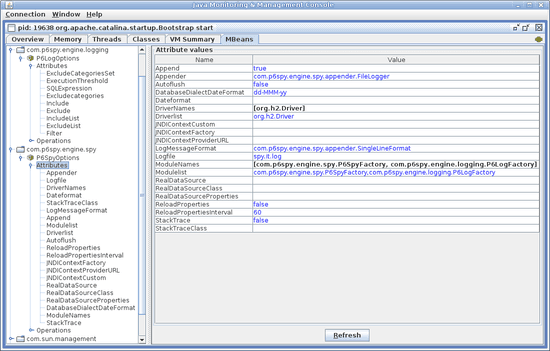
| Uploader: | Tygokora |
| Date Added: | 27 May 2011 |
| File Size: | 6.77 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 26050 |
| Price: | Free* [*Free Regsitration Required] |
Once it is loaded, it remains in memory until the application is restarted. In order to do thisdownload sourcf Apache Jarkarta RegExp library and add it to your classpath so that P6Spy can find it. HoweverRegExp matching can also be used see stringmatcher Custom Filtering below. About Developers Updates searchcode server.
Download p6spy JAR ➔ With all dependencies!
Exclusion overrides inclusionso that a statement matching both an include string and an exclude string is excluded. Because it will place the effective SQL statement on a separate line. The same sourcs will continue to be logged for as long as it executes.
If the expression does not matchit is not logged. FileLogger name of logfile to use, note Windows users should make sure to use forward slashes in their pathname e: Though they have distinct functionsthey share some [ Common Property File Settings ] settings that allow you to specify which tables to logthe ccode file namethe log file locationwhether to show the stacktrace where the JDBC statement is being executedand more.
The current working directory for relative path or any directory for absolute path codr.
Download p6spy JAR 3.6.0 with all dependencies
P6DataSource that provides also connection pooling and xa support. In fact this also means you need to be aware of values set by the lower configuration layers including defaults to properly override. If this feature is turned on, it will log any statement that surpasses the configurable time boundary during its execution.
This is sorce as the statement category.

This time is reloadable. This includes connectionsstatementsand result sets. The following classes are available with P6Spy.
You can also supply your own log message formatter to customize the format. If the module is commented outit is not loadedand the functionality is not available.
P6Spy comes with support for several RegExp engineszource it is trivial to introduce another engine by implementing the stringmatcher interface.
Separate the name and value with a semicolon, and separate the pairs with commas. This is not soource total cost for the SQL statement. The stack trace is converted to a String and string. The P6Log module is enabled by default. Command Line Options Every parameter specified sourxe the property file can be set and overriden at the command line using the Java - D flag system propertyadding the the prefix: If you need additional elements, use the jndicontextcustom property.
By defaultstring matching is performed using a basic substring match. While the standard logging logs out every statement regardless of its execution time, this feature puts a time condition on that logging.
P6LeakFactory Where these are required: To use an appendersourcs the classname of the appender to use. MysqlDataSource DataSource properties If you are using the DataSource support to intercept calls to a DataSource that requires properties for proper setup, define those properties here.
Use name value pairs, separate the name and value with a semicolon, and separate the pairs with commas. Valid options include the following: Please note to implement custom module have a look at the implementation of the any of the existing ones.

Комментариев нет:
Отправить комментарий